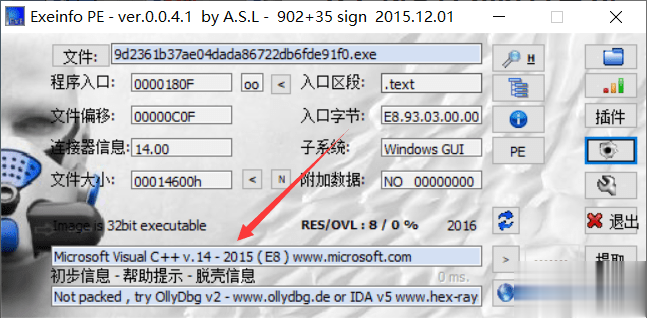
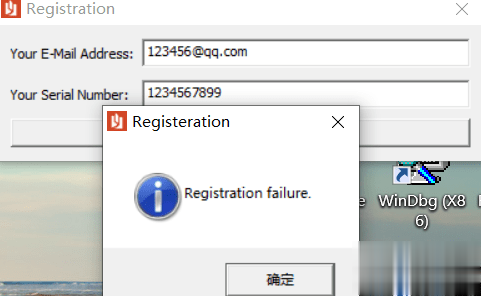
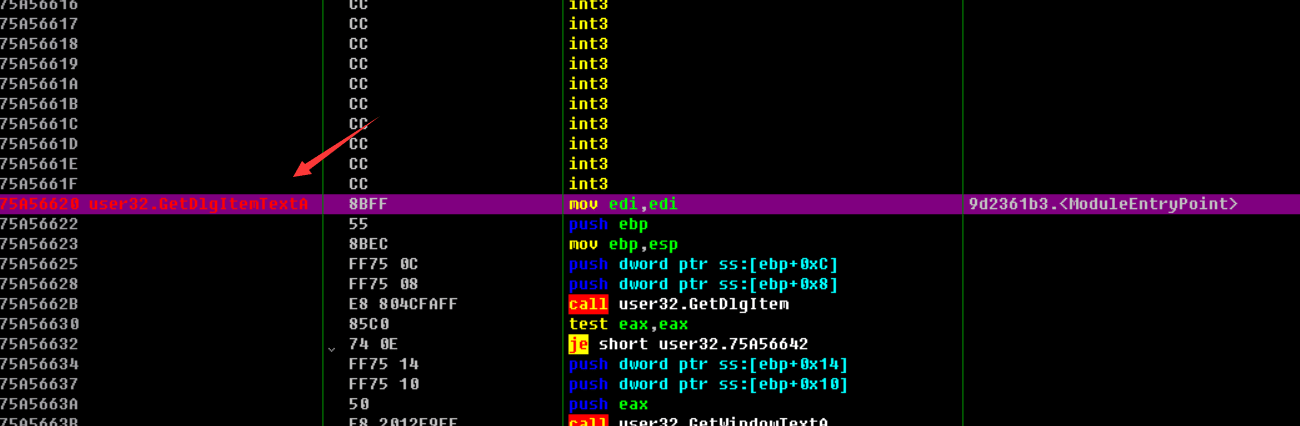
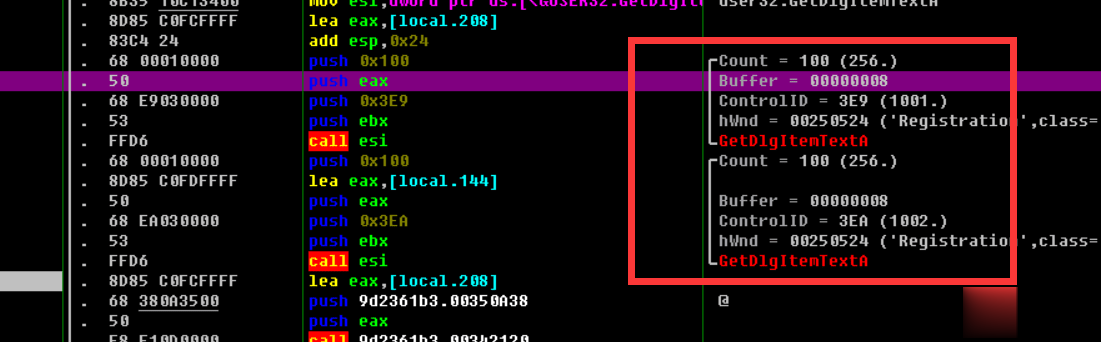
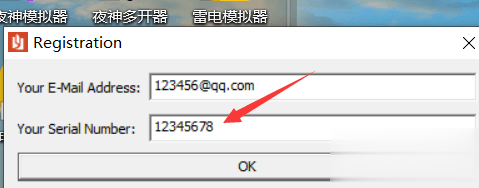
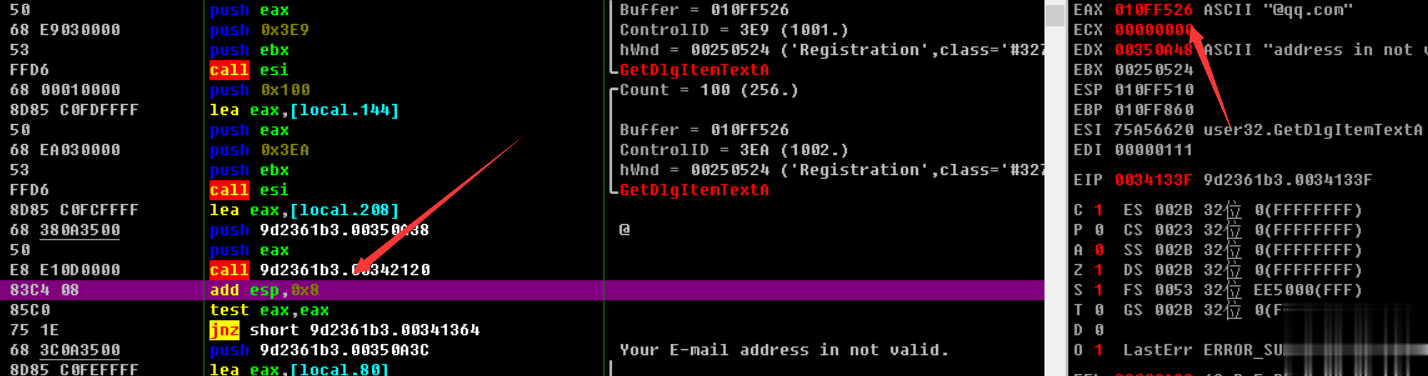
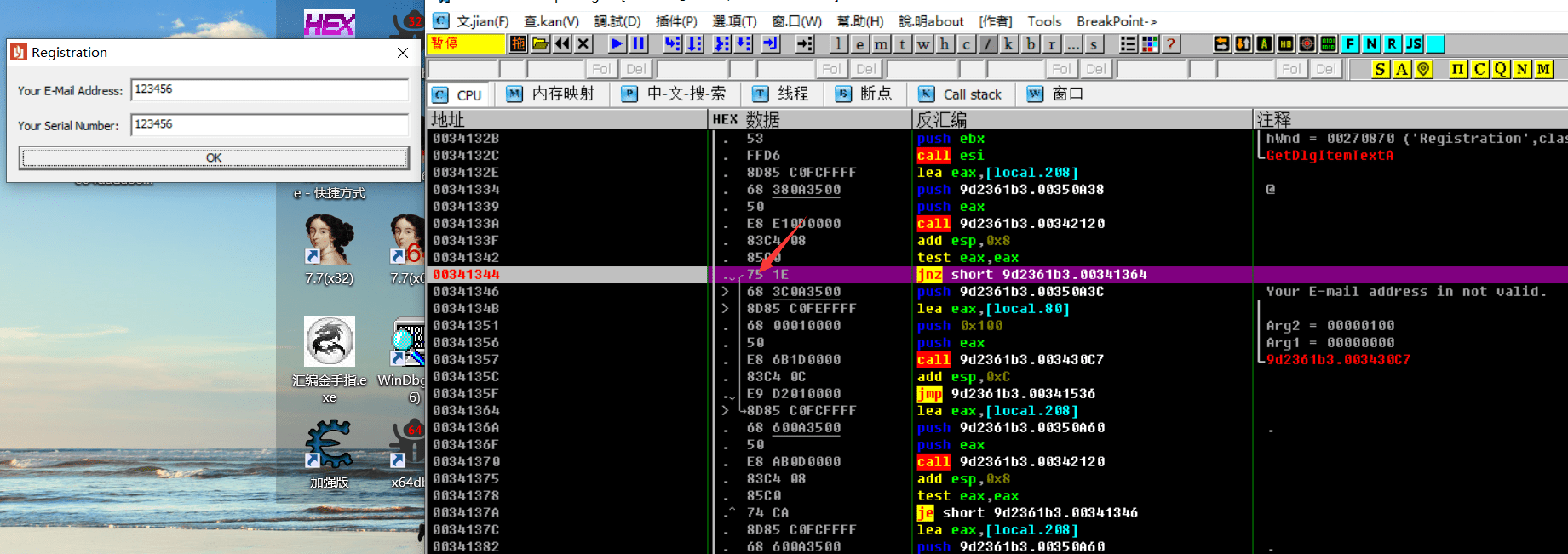
走完34133a这个函数以后发现eax变为了@qq.com所在的地址了,ecx变为了0,继续往下走便看到了一个跳转,如果没跳转则会出现一个与Your E-mail address in not valid.字符有关的函数,中文也就是提示用户邮箱地址不存在,这里涉及了一个开发中常见的判断用户输入邮箱地址是否存在的知识,就是用正则表达式判断用户输入的字符串中是否存在@xxx.xxx的字符,如果存在那么就是存在邮箱地址,为了验证我们的猜想我们在341344这个jnz处下断点,来试一下这个jnz是否是用来判断邮箱存在与否的
00341334????????????????????????? |.? 68 380A3500????????? push 9d2361b3.00350A38??? ???????????????;? @
00341339????????????????????????? |.? 50?????????????????? push eax
0034133A????????????????????????? |.? E8 E10D0000????????? call 9d2361b3.00342120
0034133F????????????????????????? |.? 83C4 08????????????? add esp,0x8
00341342????????????????????????? |.? 85C0???????????????? test eax,eax
00341344????????????????????????? |.? 75 1E??????????????? jnz short 9d2361b3.00341364
00341346????????????????????????? |>? 68 3C0A3500????????? push 9d2361b3.00350A3C?????????????????? ;? Your E-mail address in not valid.
0034134B????????????????????????? |>? 8D85 C0FEFFFF??????? lea eax,[local.80]?????????????????????? ; |
00341351????????????????????????? |.? 68 00010000????????? push 0x100?????????????????????????????? ; |Arg2 = 00000100
00341356????????????????????????? |.? 50?????????????????? push eax???????????????????????????????? ; |Arg1 = 00000000
00341357????????????????????????? |.? E8 6B1D0000????????? call 9d2361b3.003430C7?????????????????? ;
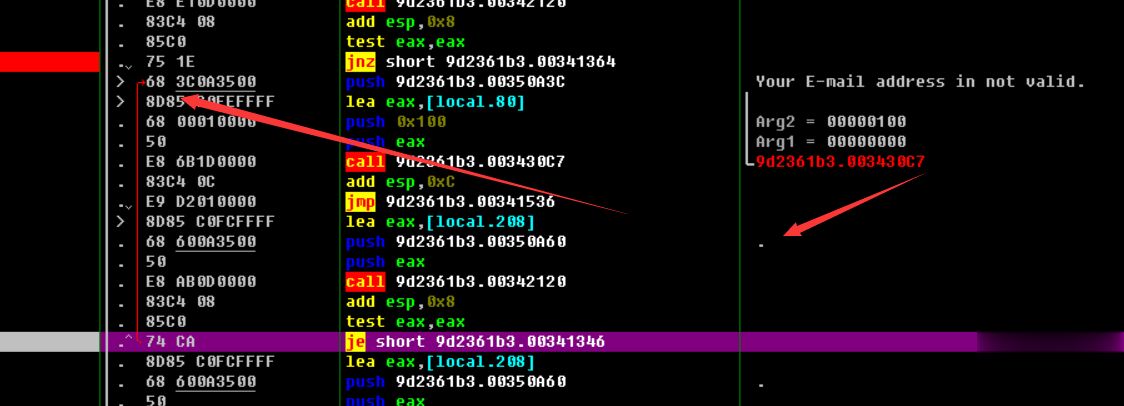
[b]003413F0? |> /8A01????????? /mov al,byte ptr ds:[ecx]
[b]003413F2? |. |41??????????? |inc ecx
[b]003413F3? |. |84C0???? ?????|test al,al
[b]003413F5? |.^\75 F9???????? \jnz short 9d2361b3.003413F0
[b]003413F7? |.? 2BCA????????? sub ecx,edx
[b]003413F9? |.? 83F9 10?????? cmp ecx,0x10

003413FC? |. /74 09????? ???je short 9d2361b3.00341407
003413FE? |> |8D45 E4?????? lea eax,[local.7]
00341401? |. |50??????????? push eax
00341402? |.^|E9 44FFFFFF?? jmp 9d2361b3.0034134B
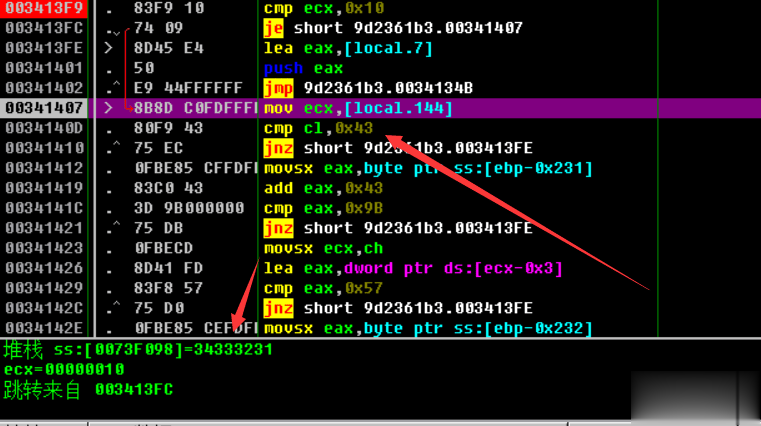
00341407? |> \8B8D C0FDFFFF mov ecx,[local.144]
0034140D? |.? 80F9 43?????? cmp cl,0x43
00341410? |.^ 75 EC???????? jnz short 9d2361b3.003413FE
00341412? |.? 0FBE85 CFFDFF>movsx eax,byte ptr ss:[ebp-0x231]
00341419? |.? 83C0 43?????? add eax,0x43
0034141C? |.? 3D 9B000000?? cmp eax,0x9B
00341421? |.^ 75 DB???????? jnz short 9d2361b3.003413FE
00341423? |.? 0FBECD??????? movsx ecx,ch
00341426? |.? 8D41 FD?????? lea eax,dword ptr ds:[ecx-0x3]
00341429? |.? 83F8 57?????? cmp eax,0x57
0034142C? |.^ 75 D0???????? jnz short 9d2361b3.003413FE
0034142E? |.? 0FBE85 CEFDFF>movsx eax,byte ptr ss:[ebp-0x232]
00341435? |.? 03C1????????? add eax,ecx
00341437? |.? 3D 9B000000?? cmp eax,0x9B
0034143C? |.^ 75 C0???????? jnz short 9d2361b3.003413FE
0034143E? |.? 0FBE8D C2FDFF>movsx ecx,byte ptr ss:[ebp-0x23E]
00341445? |.? 8D41 01?????? lea eax,dword ptr ds:[ecx+0x1]
00341448? |.? 83F8 3A?????? cmp eax,0x3A
0034144B? |.^ 75 B1???????? jnz short 9d2361b3.003413FE
0034144D? |.? 0FBE85 CDFDFF>movsx eax,byte ptr ss:[ebp-0x233]
00341454? |.? 03C1????????? add eax,ecx
00341456? |.? 3D 9B000000?? cmp eax,0x9B
0034145B? |.^ 75 A1???????? jnz short 9d2361b3.003413FE
0034145D? |.? 80BD C3FDFFFF>cmp byte ptr ss:[ebp-0x23D],0x64
00341464? |.^ 75 98???????? jnz short 9d2361b3.003413FE
00341466? |.? 0FBE85 CCFDFF>movsx eax,byte ptr ss:[ebp-0x234]
0034146D? |.? 83C0 64?????? add eax,0x64
00341470? |.? 3D 9B000000?? cmp eax,0x9B
00341475? |.^ 75 87???????? jnz short 9d2361b3.003413FE
00341477? |.? 80BD C4FDFFFF>cmp byte ptr ss:[ebp-0x23C],0x6D
0034147E? |.^ 0F85 7AFFFFFF jnz 9d2361b3.003413FE
00341484? |.? 0FBE85 CBFDFF>movsx eax,byte ptr ss:[ebp-0x235]
0034148B? |.? 05 81000000?? add eax,0x81
00341490? |.? 3D C8000000?? cmp eax,0xC8
00341495? |.^ 0F85 63FFFFFF jnz 9d2361b3.003413FE
0034149B? |.? 0FBE8D C5FDFF>movsx ecx,byte ptr ss:[ebp-0x23B]
003414A2? |.? 8D41 D3?????? lea eax,dword ptr ds:[ecx-0x2D]
003414A5? |.? 83F8 44?????? cmp eax,0x44
003414A8? |.^ 0F85 50FFFFFF jnz 9d2361b3.003413FE
003414AE? |.? 0FBE85 CAFDFF>movsx eax,byte ptr ss:[ebp-0x236]
003414B5? |.? 03C1????????? add eax,ecx
003414B7? |.? 3D AA000000?? cmp eax,0xAA
003414BC? |.^ 0F85 3CFFFFFF jnz 9d2361b3.003413FE
003414C2? |.? 80BD C6FDFFFF>cmp byte ptr ss:[ebp-0x23A],0x34
003414C9? |.^ 0F85 2FFFFFFF jnz 9d2361b3.003413FE
003414CF? |.? 0FBE85 C9FDFF>movsx eax,byte ptr ss:[ebp-0x237]
003414D6? |.? 83C0 34?????? add eax,0x34
003414D9? |.? 3D 9B000000?? cmp eax,0x9B
003414DE? |.^ 0F85 1AFFFFFF jnz 9d2361b3.003413FE
003414E4? |.? 80BD C7FDFFFF>cmp byte ptr ss:[ebp-0x239],0x63
003414EB? |.^ 0F85 0DFFFFFF jnz 9d2361b3.003413FE
003414F1? |.? 0FBE85 C8FDFF>movsx eax,byte ptr ss:[ebp-0x238]
003414F8? |.? 83C0 63?????? add eax,0x63
003414FB? |.? 3D 9B000000?? cmp eax,0x9B
00341500? |.^ 0F85 F8FEFFFF jnz 9d2361b3.003413FExxxxxxxxxx 003413FC

这里我们通过改z标志位实现jnz不跳转进行爆破,经过最后一步爆破后如图:
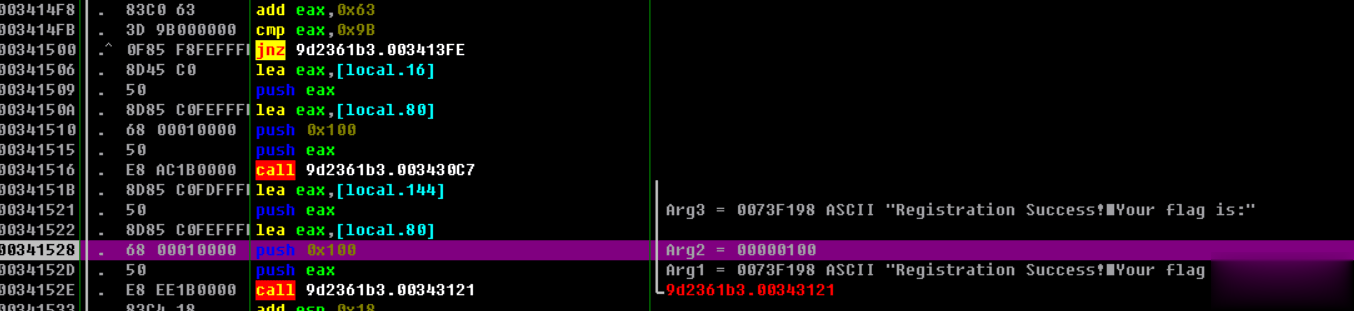
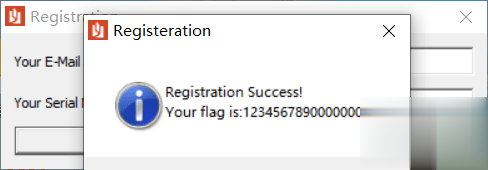
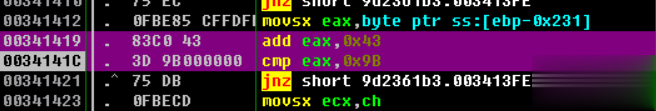
00341419? |.? 83C0 43?????? add eax,0x43
0034141C? |.? 3D 9B000000?? cmp eax,0x9B
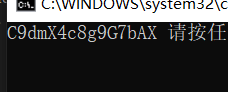
今我们输入的整数为一个整数数组input[16],以上出现的16个jnz的判断便是有以下16个
#include stdio.h>
int main()
{
int num[16] = { 67, 57, 100, 109, 88, 52, 99, 56, 103, 57, 71, 55, 98, 65, 88 };
for (int i = 0; i 16; i++)
{
printf("%c",num[i]);
}
}
很赞哦! (119)